Mitigate WannaCry Ransomware
WannaCry or WannaCrypt is encrypting many systems. Don't be a victim.
Patch your systems
WannaCry is ransomware that infects systems via a vulnerability that was patched in March, 2017, MS17-010.
To protect yourself from the current version of WannaCry, patch all your systems immediately and make sure MS17-010 is applied.
No Kill Switch variant released
There was a particular DNS site initial versions of WannaCry checked before initiating its attack. Interestingly, if the Domain queried wasn't registered, the malware executed. MalwareTech was able to stop the ransomware using this kill switch by registering the domain and sending requests to a sink hole.
MalwareTech believes the kill switch was likely bad logic by the creators of WannaCry in trying to halt malware analysts. Sandboxes used to analyze malware typically answer all DNS queries with a local IP Address, even for domains that aren't registered. If the malware stops when the unregistered domain responds, it hinders further analysis.
That kill switch, intentional or not, has been removed as MalwareTech predicted it would be, and the malware will now run amok, automatically scanning for and infecting any vulnerable systems it finds.
Nmap Scripting Engine (NSE) Script released
If you have a large environment, and aren't sure whether your infrastructure contains vulnerable systems, you can use conventional scanning tools like Tenable Nessus or Qualys, but if you want to quickly scan a large range of devices specifically for this vulnerability, an NSE script is available for it.
Learn more about using NSE Scripts.
Protect yourself from ransomware
I published this post earlier this month arming you with free steps and tools to protect yourself from ransomware. It may be worth another look.
Two free tools that may help
- RansomFree by Cybereason is the Windows utility.
- RansomWhere? is the Mac OSX tool.
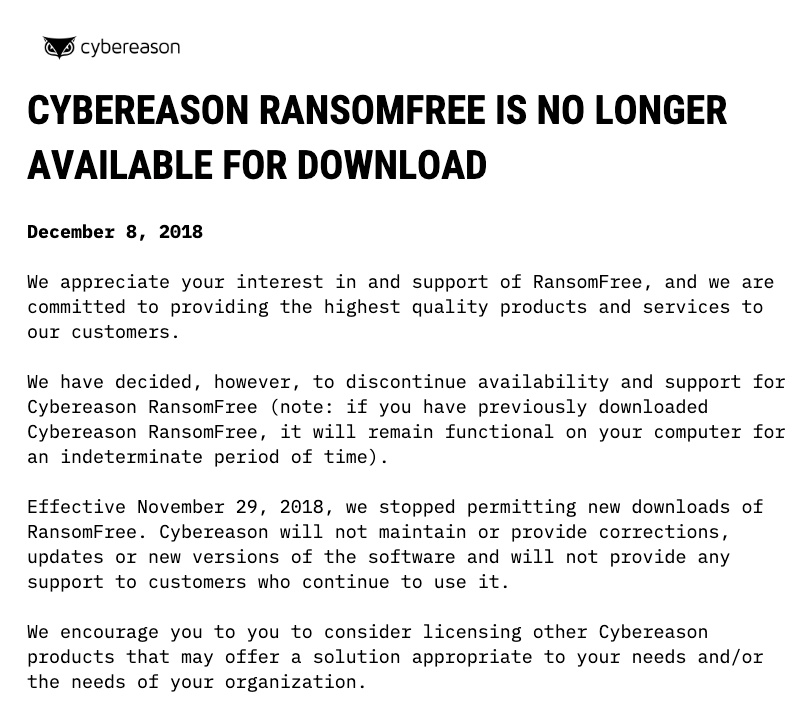
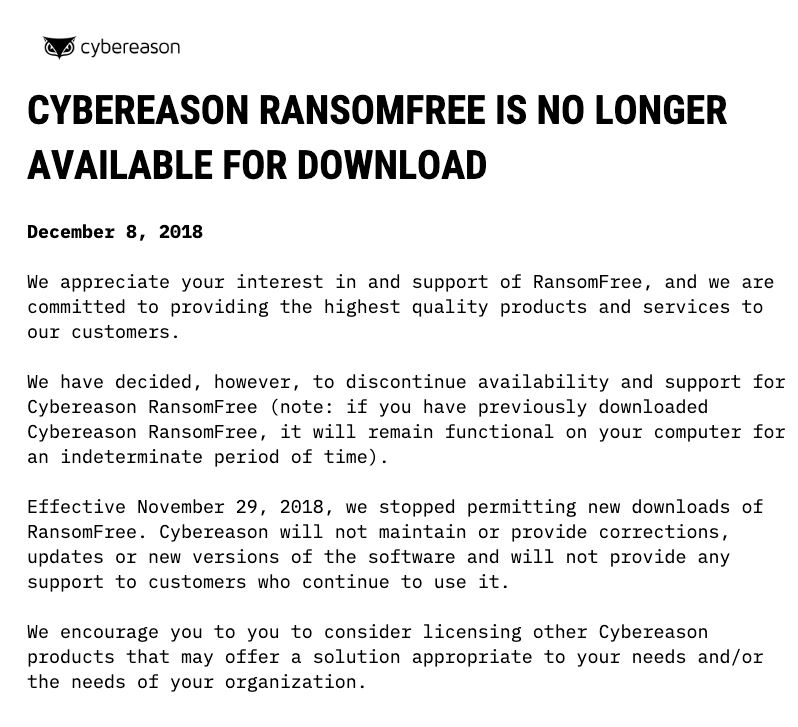
[update] So sorry, but it looks as though RansomFree is no longer available. You may find a suitable replacement here.
I'll keep an eye out for an alternative and post when I find something.
I've used both and they're lightweight and free, but it isn't clear to me that they'll stop WannaCry as it isn't user initiated activity. An interesting thing to try in a sandboxed environment.
A key to protecting yourself from WannaCry is updating your systems!
Keeping offline backups is also helpful if you do get infected.
Check out MalwareTech's WannaCry infection map.
Awesome work by MalwareTech! He says he was just doing his daily routine, but it saved many, many people and organizations from being infected, and gave the world time to react. Microsoft even released a patch for outdated systems to counter the threat. Brian Krebs wrote an article about it.
Stay safe!

