What Google's QUIC Protocol is and Why It Matters
Quick UDP Internet Connections Protocol or QUIC for short is a protocol created by Google that allows access to content, including YouTube, on using Google's Chrome browser and on Google devices.
Secure Hypertext Transfer Protocol (HTTPS), uses Transmission Control Protocol (TCP), as does Hypertext Transfer Protocol (HTTP). Transmission Control Protocol is connection oriented or stateful. HTTPS uses TCP port 443, and HTTP uses TCP port 80.
In order to start exchanging data with a web site using HTTP or HTTPS, a three-way handshake must occur, and there's a method for tracking each packet of data and knowing whether it was received and what order it should be in.
All this handshaking and tracking of packets creates overhead for the requestor and the server. On the requestor's end, the difference in bandwidth consumed and time it takes for a page to display likely isn't noticeable. On the server side, especially with a site like Google, processing millions of requests per second, the difference can really add up!
Google's QUIC protocol uses User Datagram Protocol (UDP) over ports 80 and 443. Non-encrypted QUIC traffic uses UDP 80, and encrypted traffic is sent over UDP 443.
UDP is connectionless. It's a best effort, fire and forget protocol. The requestor sends the request to the server without knowing or caring, at the protocol level, whether the server received the request. The requesting application is then tasked with tracking whether a response is received.
Given how reliable Internet service has become over much of the world, the likelihood of dropped packets causing issues is relatively low and the bandwidth saved in not having to use a connection oriented protocol seems like an acceptable tradeoff.
All good, and I have no qualms about saving bandwidth for consumers and suppliers of Internet content.
An issue arises, however, when a company has a policy against using social media at work, and attempts to enforce the policy using technology like a Next Generation Firewall (NGFW), or web filtering.
NGFW's and web filters look for traffic on TCP ports 443 and 80, not on UDP ports 443 and 80. This means traffic to social media sites, primarily ones operated by Google, including YouTube, may quietly transfer viewers over to using QUIC. This has the effect of bypassing any filtering that looks for normal HTTP or HTTPS traffic.
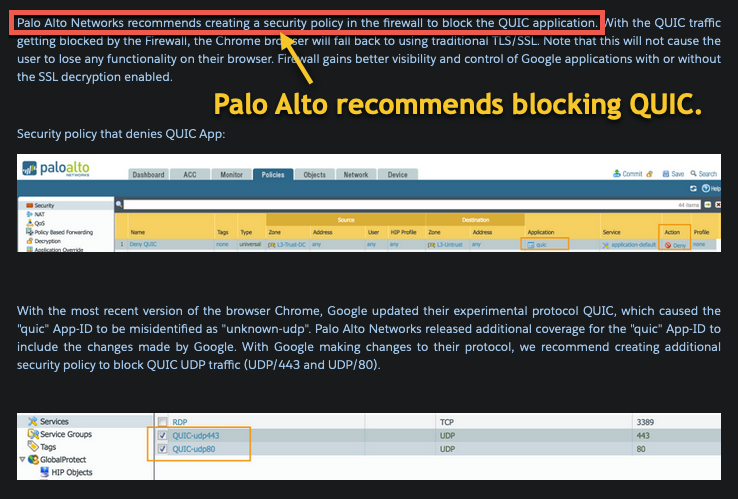
Palo Alto Networks, a huge vendor of NGFW's, recommends blocking QUIC protocol for customers trying to manage web traffic. To do this, simply create a rule that does not allow UDP ports 80 and 443 outbound.
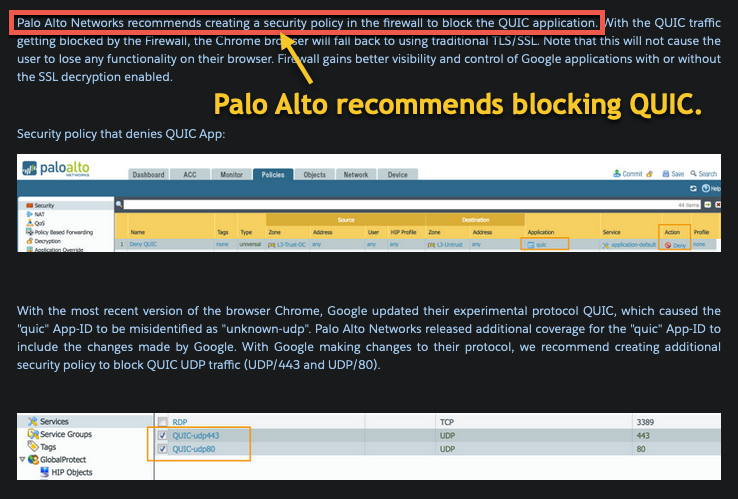
Blocking QUIC should not be noticeable to users, since their browsers will fall back to standard HTTP/HTTPS support.
QUIC is a default where it's available for Google Chrome and Google devices like the Chromebook. Other browsers are exploring support of QUIC but it is unclear whether it will become a default.
In summary, while QUIC saves some bandwidth and may be useful in many cases, it could bypass some of your web filtering efforts if allowed. You can block its use if it results in users bypassing your web flitering if desired without noticeably impacting their experience.
Here's Google's whitepaper on the QUIC protocol for those interested in reading further.