Using Your Modern Honeynet (MHN)
What you'll see when running a server and sensors
In previous posts, I covered creating an MHN Server and deploying MHN Sensors. This post shows you some of MHN's capabilities.
Server Side
On the server, you can observe the following via the web interface.
Map
See a map updated near real-time of attack sources and targets.

Deploy
Deploy new sensors as covered in a previous post.
Attacks
View near real-time data on attacks hitting your sensors.

Payloads
Download and interact with actual payloads deposited in hacking attempts on your sensors. Use extreme caution with these. They are likely live exploits. You will want to have a segregated environment and experience doing malware analysis.

Rules
You can view rules for applicable sensors like Snort rules here.

Sensors
View deployed sensors and the number of hits they've received.

Charts
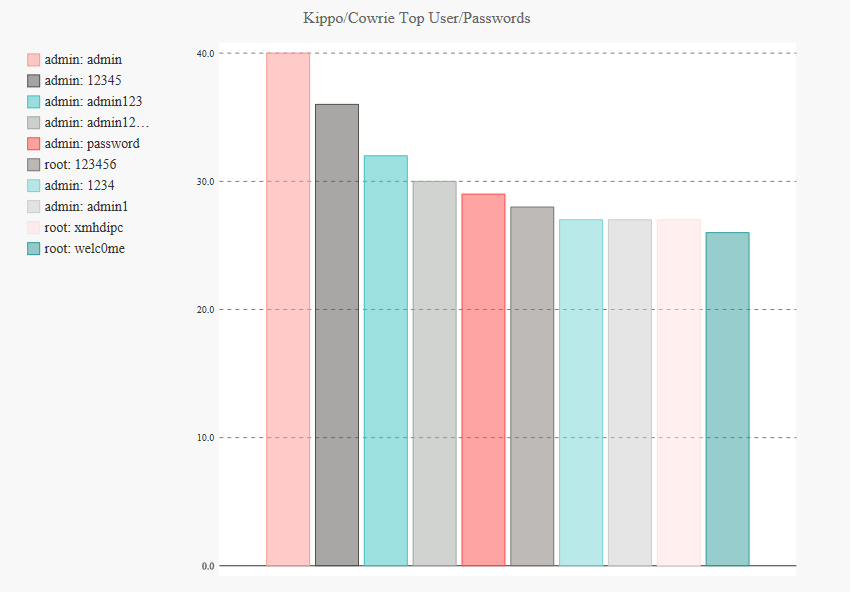
You can view some interesting statistics from Kippo and Cowrie sensors here including top passwords and usernames observed in attacks and top attackers.
Top captured usernames and passwords:

Kippo/Cowrie top attackers:

On Honeypots
On the individual honeypots, you can look further at the information collected. Some may not be readily visible on the MHN Server.
Consult the project site for the individual honeypot you're interested in exploring deeper for more information.